Tendencies

Rikki, the most discreet and secure cold wallet
Throughout so many articles on bank card security, we have learned: As security in the technological world increases, we users are becoming the most valuable target for cybercriminals . For...
Rikki, the most discreet and secure cold wallet
Throughout so many articles on bank card security, we have learned: As security in the technological world increases, we users are becoming the most valuable target for cybercriminals . For...

When you are no longer you
Having our phone stolen always hurts, but that's not the worst thing that can happen. The worst is having our digital identity stolen. In this case, we have no choice...
When you are no longer you
Having our phone stolen always hurts, but that's not the worst thing that can happen. The worst is having our digital identity stolen. In this case, we have no choice...

Phishing, when no one is who they say they are
The main objective of phishing is to obtain our banking information, but it is not the only objective. In fact, Little is said about the consequences of this type of...
Phishing, when no one is who they say they are
The main objective of phishing is to obtain our banking information, but it is not the only objective. In fact, Little is said about the consequences of this type of...

I lost my phone, what now?
As we've seen, users are the most vulnerable part of the security system, so here are some tips to help you avoid regrets if you ever lose your phone or...
I lost my phone, what now?
As we've seen, users are the most vulnerable part of the security system, so here are some tips to help you avoid regrets if you ever lose your phone or...

The card in the mobile wallet, nice and warm...
There's no doubt that paying with your mobile phone is a rapidly expanding practice. In this and the next two articles, we examine the security benefits of this payment method,...
The card in the mobile wallet, nice and warm...
There's no doubt that paying with your mobile phone is a rapidly expanding practice. In this and the next two articles, we examine the security benefits of this payment method,...
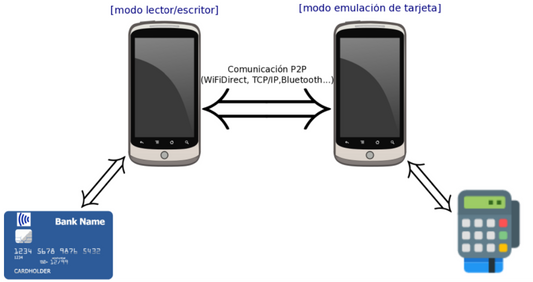
Contactless payment security tested in laborato...
When a new security standard is launched, the first thing experts outside the system do is stress-test it to detect vulnerabilities. And, of course, contactless payment using an EMV-certified NFC...
Contactless payment security tested in laborato...
When a new security standard is launched, the first thing experts outside the system do is stress-test it to detect vulnerabilities. And, of course, contactless payment using an EMV-certified NFC...