Contactless payment security tested in laboratories
Share
Image: CCN-CERT
Relay attacks
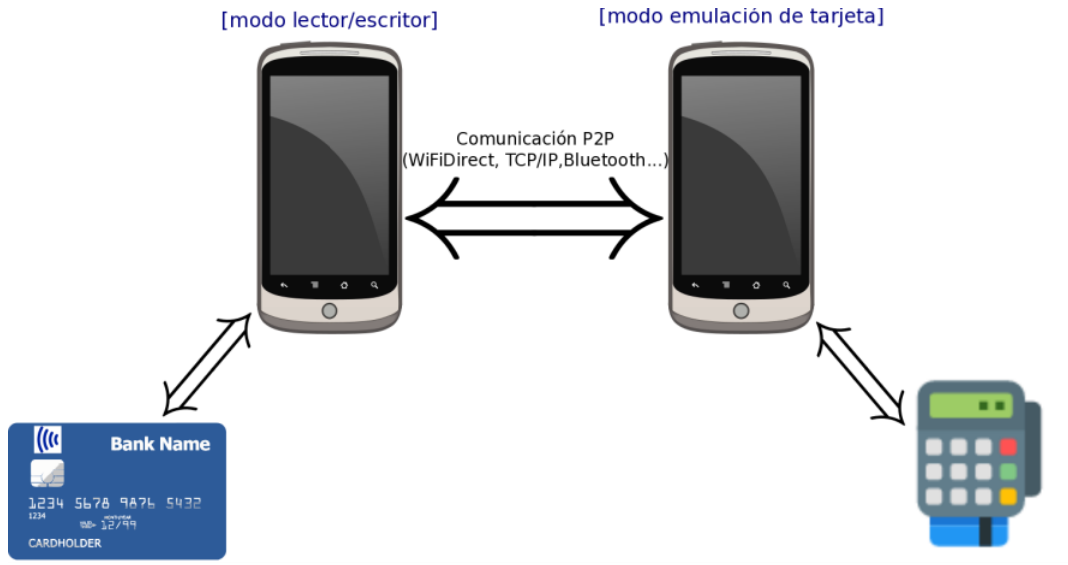
These types of attacks aim to capture data in flight while a contactless payment is being processed and retransmit it over long distances to malicious terminals. They are based on the man-in-the-middle approach, meaning a third party (the thief) captures the communication established between two trusted points (the card and the POS terminal, or the POS and the payment processor's servers), posing as the server when the POS terminal requests it, or as the POS terminal when the server requests it.
In theory, it would be enough for one of the thieves to use a smartphone with relatively easy-to-obtain software to capture the card data and transmit it to an accomplice located miles away with another smartphone in one hand and a POS terminal in the other. Or, in a more stable version, they would retransmit the signal via Bluetooth to an accomplice located a few meters away.
As we've said, in practice, getting the smartphone to behave as expected within the barriers imposed by the physics of NFC signals and maintain uninterrupted long-distance communication in an urban environment filled with interference isn't easy, since capturing the transaction requires the entire process to be completed in real time and in less than 5 seconds. However, the transaction data could be saved for later playback, but in that case, the bank would reject the transaction for not complying with the EMV protocol.
Eavesdropping attacks
This type of attack takes advantage of some well-known vulnerabilities in EMV cards: transmitting sensitive data in the open and not verifying which device they're talking to, for example, not knowing whether the caller is a POS terminal or a smartphone. Anyone can verify this by installing an EMV card reader on their mobile phone.
This means anyone can access the public information on any EMV-enabled bank card: the PAN, cardholder, expiration date, and transaction history—enough for many American merchants to process a payment.
The idea behind this type of attack is to expand the coverage area of the electromagnetic waves emitted by the NFC chip, which in practice can extend up to 30 or 40 cm. However, achieving this requires sophisticated hardware and software , but above all, the attacker must approach you with a laptop and a half-meter antenna, be within the card's coverage area while you are paying, and both points, the card and the dataphone, must remain stationary so that communication is not interrupted . While this scenario is ridiculous on the terrace of a bar, it could be plausible in a small business controlled by a criminal organization. In any case, there is no record of it having occurred.